Disaster Recovery Planning Checklist - 2025 Essentials
#disaster-recovery-planning-checklist#business-continuity#IT-disaster-recovery#risk-management#cyber-resilience
October 28, 2025
In today's interconnected business environment, the question isn't if a disruption will occur, but when. From sophisticated cyberattacks and critical hardware failures to natural disasters and simple human error, an unforeseen event can instantly halt operations, irrevocably damage your brand reputation, and lead to catastrophic financial loss. A purely reactive approach to crisis management is a gamble organizations can no longer afford to take. Proactive, meticulous preparation through a robust disaster recovery (DR) plan is the only reliable path to genuine business resilience.
This comprehensive disaster recovery planning checklist is your definitive guide to building that resilience. We will break down the 10 most essential, actionable steps your organization must take to protect its critical assets, ensure business continuity, and recover swiftly when the worst happens. Moving beyond abstract theories, each item on this list provides a practical framework for implementation, covering everything from risk assessment and backup strategies to team roles and plan validation.
Each step is designed to build logically upon the last, helping you construct a fortified strategy that is not just documented but also practical and testable. Following this checklist will empower you to transform your organization from a potential victim of circumstance into a prepared and resilient enterprise, ready to face any disruption with confidence and a clear plan of action. This guide provides the blueprint for that transformation, ensuring you have the structure needed to protect your data, your clients, and your future.
1. Conduct a Business Impact Analysis (BIA)
Before you can create a disaster recovery plan, you must first understand what you are protecting and why. A Business Impact Analysis (BIA) is the foundational step in any effective disaster recovery planning checklist. It's a systematic process that identifies your most critical business functions and quantifies the potential effects of their disruption.
A BIA moves beyond IT infrastructure to focus on the business itself. It answers crucial questions like, "What are our most time-sensitive operations?" and "What would be the financial and operational cost if a specific process went down for an hour, a day, or a week?" This analysis forms the basis for all subsequent recovery decisions, ensuring that resources are allocated to protect the most vital components of your organization.
How a BIA Establishes Recovery Priorities
The primary outputs of a BIA are the Recovery Time Objective (RTO) and the Recovery Point Objective (RPO) for each business function.
- RTO: The maximum acceptable downtime for a system or function before the business suffers significant damage.
- RPO: The maximum acceptable amount of data loss, measured in time. An RPO of one hour means the business can tolerate losing up to one hour of data.
For example, an e-commerce company's BIA would likely assign a very low RTO and RPO (mere minutes) to its payment processing system, as any downtime directly translates to lost revenue. Conversely, an internal HR reporting system might have a higher RTO of 24 hours, as its immediate unavailability is less impactful.
Key Insight: A BIA is not just an IT exercise; it is a business strategy tool. It provides the data-driven justification needed to secure budget and executive support for your disaster recovery initiatives.
Actionable Tips for an Effective BIA:
- Involve All Departments: Interview stakeholders from every business unit, from finance to sales to operations. They possess the ground-level knowledge to identify truly critical processes that IT might overlook.
- Create Criticality Tiers: Group applications and functions into tiers (e.g., Tier 1: Mission-Critical, Tier 2: Business-Critical, Tier 3: Non-Essential). This simplifies decision-making during a crisis.
- Document Dependencies: Meticulously map out the relationships between systems, applications, and business processes. A seemingly low-priority application might be essential for a Tier 1 function to operate.
- Update Annually: Your business is not static. Revisit and update your BIA at least once a year or whenever there's a significant change, such as the launch of a new product or a major system migration.
2. Establish a Disaster Recovery Team and Define Roles
A plan is only as effective as the people who execute it. Establishing a dedicated Disaster Recovery (DR) team with clearly defined roles is a critical step in any disaster recovery planning checklist. Technology and backups are essential, but human coordination and decisive leadership are what truly navigate a crisis successfully.
This team acts as the central command during a disaster, responsible for activating the plan, coordinating response efforts, and communicating with stakeholders. Simply listing names is not enough; each member must understand their specific duties, the chain of command, and who their backup is if they are unavailable. This structure prevents confusion and delay when every second counts.
How a DR Team Ensures Coordinated Response
The primary purpose of a formal team is to eliminate ambiguity during a high-stress event. Roles are pre-assigned, and responsibilities are understood before an incident occurs, enabling a swift and organized response.
- Recovery Manager: The overall leader who declares a disaster, activates the plan, and serves as the primary decision-maker.
- Technical Leads: Specialists responsible for restoring specific systems, such as networks, servers, or critical applications, according to the BIA's priorities.
- Communications Coordinator: The designated point of contact for all internal and external communications, ensuring consistent and accurate messaging to employees, customers, and the media.
For example, large organizations like Microsoft structure their DR teams with regional coordinators who can act autonomously, while financial services firms often maintain 24/7 on-call teams to ensure immediate response capability, reflecting their extremely low RTOs.
Key Insight: A disaster recovery plan without a designated team and defined roles is merely a document. A well-structured team turns that document into an actionable, effective response mechanism.
Actionable Tips for Building Your DR Team:
- Create a RACI Matrix: For each recovery task, clearly document who is Responsible, Accountable, Consulted, and Informed. This simple chart removes any doubt about ownership.
- Maintain an Up-to-Date Contact Tree: Keep a secure list of primary and secondary contact details (mobile, home, email) for all team members, accessible even if primary systems are down.
- Document Succession Planning: Every critical role, especially the Recovery Manager, must have at least one designated successor who is trained and ready to step in at a moment's notice.
- Include Cross-Functional Representation: Your team should not be limited to IT. Involve members from key departments like operations, communications, legal, and senior management to ensure a holistic response.
3. Create a Backup and Recovery Strategy
With your critical systems identified, the next step in any disaster recovery planning checklist is to establish how you will protect and restore your data. A backup and recovery strategy is the technical backbone of your plan, outlining the specific processes, technologies, and policies needed to ensure data is copied, stored securely, and can be retrieved effectively after a disruption.
This strategy moves beyond simply "backing up files." It's a comprehensive approach that dictates backup frequency, storage locations, data retention periods, and the exact methods for restoration. A well-designed strategy ensures that the data you recover is current enough (meeting your RPO) and can be restored fast enough (meeting your RTO) to prevent significant business harm.
How a Backup Strategy Ensures Data Resilience
A robust backup and recovery strategy is built on principles of redundancy and verification. It is not enough to have a single copy of your data; you need multiple copies in different locations and on different media to protect against a wide range of threats, from hardware failure to a regional catastrophe.
- The 3-2-1 Rule: A widely adopted best practice for data protection. It dictates you should have at least three copies of your data, on two different types of media, with one of those copies located off-site.
- Replication vs. Backup: For mission-critical systems with near-zero RPOs, continuous data protection (CDP) or replication might be necessary. Unlike traditional backups that are periodic, replication creates a real-time or near-real-time copy of data in a secondary location.
For example, a company might use a service like AWS Backup to automate daily backups of its servers to the cloud, satisfying one off-site copy. For its mission-critical database, it might also implement real-time replication to a secondary data center to achieve a zero RPO.
Key Insight: Your backup strategy is only as good as your ability to restore from it. Backups that are not regularly tested are not reliable assets; they are unverified liabilities.
Actionable Tips for an Effective Backup Strategy:
- Automate Everything: Manual backups are prone to human error and inconsistency. Automate your backup schedules to ensure they run reliably without intervention.
- Test Restorations Monthly: Schedule and perform regular tests to restore files, applications, or entire systems from your backups. This verifies data integrity and familiarizes your team with the recovery process.
- Geographically Disperse Backups: Store at least one backup copy in a location that is geographically separate from your primary site to protect against natural disasters like floods, hurricanes, or earthquakes.
- Document and Label Meticulously: Clearly document your backup procedures, schedules, and storage locations. Label all backup media so you can quickly identify the correct data set during a high-stress recovery scenario.
4. Document Critical Systems and Dependencies
Once you have identified critical business functions through a BIA, the next logical step is to map those functions to the underlying technology that supports them. Documenting critical systems and their dependencies is a foundational element of any disaster recovery planning checklist. It involves creating a comprehensive inventory of all hardware, software, applications, and data crucial for operations, and meticulously charting how they connect and rely on one another.
This documentation serves as the technical blueprint for your recovery efforts. Without a clear understanding of your IT environment and its intricate connections, you cannot execute an effective recovery. You wouldn't know which server to restore first, which database is tied to a critical application, or which network switch supports the entire sales department. This detailed inventory ensures that recovery is an orderly, sequential process, not a chaotic guessing game.
How Documentation Enables Efficient Recovery
The primary goal of this documentation is to establish a single source of truth for your IT infrastructure, which is indispensable during a high-stress disaster scenario. It defines the "what" and "how" of your recovery sequence, ensuring that foundational systems are brought online before the applications that depend on them.
- System Inventory: A detailed list of every critical server, network device, storage array, and software application, including configurations, versions, and physical locations.
- Dependency Mapping: A visual and written record of how systems interact. For example, a dependency map would show that your e-commerce website relies on a specific product database, which in turn relies on a particular storage server.
A financial institution, for instance, would maintain detailed maps showing how its core banking application connects to authentication servers, transaction databases, and third-party payment gateways. This ensures they can restore services in the correct order to avoid data corruption and further outages.
Key Insight: Comprehensive documentation is your recovery team's roadmap in the dark. During a crisis, there is no time for discovery; you need a pre-defined, accurate guide to rebuild your environment efficiently and correctly.
Actionable Tips for Effective Documentation:
- Use Automated Discovery Tools: Leverage tools like SolarWinds or Lansweeper to build an initial, comprehensive inventory of your assets. This automates a time-consuming process and reduces human error.
- Create Visual Dependency Maps: Use diagramming software like Visio or Lucidchart to create clear, visual representations of how applications and infrastructure are interconnected. A picture is often easier to interpret during a crisis.
- Include Vendor and Contact Information: For each critical system, document vendor support contacts, contract numbers, and internal system owners. This information is vital when you need to escalate an issue quickly.
- Maintain an Offline Copy: Store a physical or electronically isolated copy of this critical documentation in a secure, offsite location. You cannot rely on accessing documentation that is stored on the very systems that have failed.
5. Identify and Secure Alternate Recovery Sites
A robust disaster recovery planning checklist must address the physical location where operations will resume if your primary site becomes inaccessible. Identifying and securing an alternate recovery site is a critical step that ensures business continuity when faced with a regional outage, natural disaster, or any event that compromises your main facility. This involves choosing a location and a service model that aligns with the recovery objectives established in your BIA.
An alternate site is more than just a backup location; it's the operational heart of your company during a crisis. The choice of site, from a fully equipped hot site to a flexible cloud-based solution, directly impacts how quickly you can restore critical functions and resume serving customers. This decision balances cost, speed, and capability, making it a cornerstone of your recovery strategy.
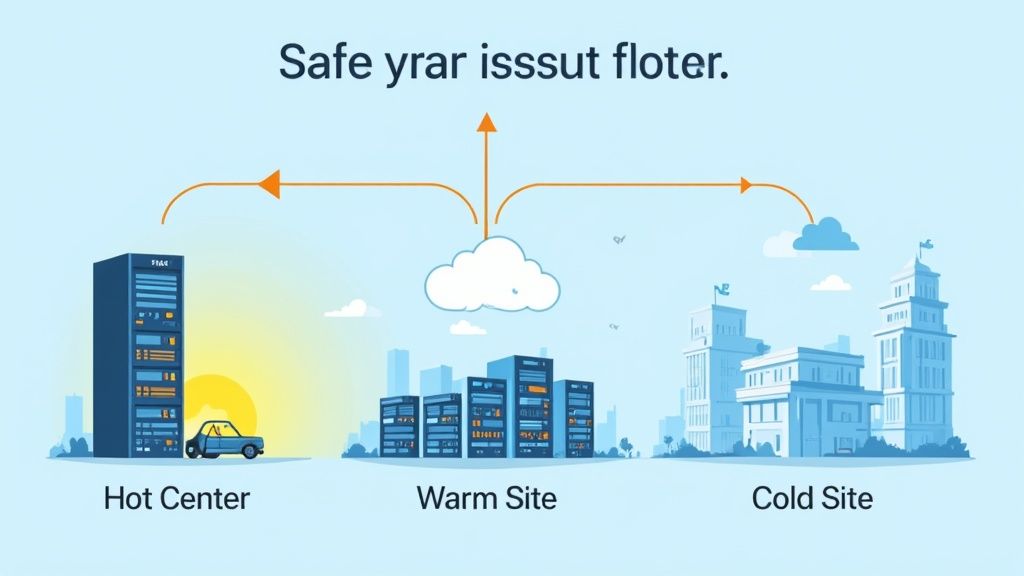
How Recovery Sites Enable Business Continuity
The primary goal of a recovery site is to provide the infrastructure, connectivity, and environment needed to failover your critical systems. The type of site you choose dictates the speed and completeness of this transition.
- Hot Site: A fully operational duplicate of your primary site with hardware, software, and real-time data synchronization. Major financial institutions often use hot sites for near-instantaneous failover.
- Warm Site: A partially equipped facility with infrastructure and hardware but requires the latest data backups to be loaded. Healthcare systems may use HIPAA-compliant warm sites for a balance of cost and recovery speed.
- Cloud-Based DR (DRaaS): Utilizes cloud providers like AWS or Azure to host replicated systems. This offers scalability and a pay-as-you-go model, popular across many industries for its flexibility.
For instance, an e-commerce platform might leverage a cloud-based DR solution to spin up its entire production environment in a different geographic region within minutes, ensuring minimal disruption to online sales.
Key Insight: Your choice of recovery site is a direct reflection of your risk tolerance and business priorities. It's a strategic investment that buys you resilience, not just a backup facility.
Actionable Tips for Selecting a Recovery Site:
- Analyze Total Cost of Ownership (TCO): Look beyond the monthly fee. Factor in costs for network links, software licensing, and personnel required to manage and test the site.
- Verify Geographic and Network Diversity: Ensure the site is far enough from your primary location to avoid being affected by the same regional disaster, but close enough for acceptable network latency if data synchronization is required.
- Establish Clear Service Level Agreements (SLAs): Your contract with a site provider must clearly define RTOs, RPOs, and the specific resources guaranteed during a declared disaster.
- Document Access and Security Protocols: Create detailed procedures for how your team will physically or virtually access the recovery site, including security credentials, contact lists, and operational steps.
6. Develop Communication and Notification Procedures
When a disaster strikes, technology is only half the battle. The other half is managing the human element through clear, timely, and consistent communication. A well-defined communication plan is an essential part of any disaster recovery planning checklist, ensuring that chaos is minimized and stakeholders are kept informed, which helps maintain trust and control the narrative.
This plan moves beyond simply notifying IT staff of an outage. It's a comprehensive strategy for engaging employees, customers, leadership, and even regulatory bodies. It answers critical questions like, "Who needs to be told what, and when?" and "How will we deliver these messages if our primary channels are down?" In the absence of official information, rumors and misinformation can spread rapidly, causing more damage than the initial incident.
How a Communication Plan Maintains Order
A robust communication plan establishes a clear hierarchy and predefined messaging for various scenarios, preventing confusion during a high-stress event. The core components are pre-approved templates and a designated chain of command.
- Templates: Pre-written messages for different audiences (internal, external, regulatory) and disaster types (outage, data breach, physical disaster) that can be quickly adapted and deployed.
- Chain of Command: Clearly defined roles specifying who is authorized to communicate with the public, who coordinates internal updates, and who contacts key partners or vendors.
For example, the response to the 2017 Equifax data breach was widely criticized for its slow and confusing communication, which eroded public trust. In contrast, a well-prepared organization would have a designated spokesperson and templated initial statements ready to deploy, ensuring a swift and unified message that acknowledges the issue and outlines the next steps.
Key Insight: In a crisis, effective communication is as critical as technical recovery. A failure to communicate properly can turn a manageable IT incident into a major public relations disaster, causing lasting damage to your brand's reputation.
Actionable Tips for an Effective Communication Plan:
- Create Pre-approved Templates: Draft and get legal/executive approval for communication templates covering various scenarios. Include messages for social media, email, website banners, and press releases.
- Establish a Communication "War Room": Designate a central team, including representatives from IT, HR, legal, and PR, to coordinate all crisis communications and ensure message consistency.
- Use Multi-Channel Alerts: Don't rely on a single communication method. Plan to use a combination of email, SMS text alerts, a dedicated status page, and social media to reach all stakeholders.
- Define Update Cadence: Commit to a public schedule for updates, even if there is no new information. A simple "We are still investigating and will provide another update in two hours" is better than silence.
7. Test and Validate Disaster Recovery Plans
A disaster recovery plan that has never been tested is merely a collection of assumptions. Testing and validating your plan is the critical step that transforms theory into a proven, reliable process. This involves regularly executing drills to verify that procedures work as intended, systems recover within their objectives, and all team members understand their specific roles during a crisis.
Testing moves your disaster recovery planning checklist from a static document to a living, validated strategy. It uncovers flaws, gaps in documentation, and incorrect assumptions that would otherwise only surface during a real emergency. From simple tabletop exercises to full-scale failovers, each type of test provides a different level of assurance, building organizational confidence in its ability to respond and recover effectively.
How Testing Ensures Plan Viability
The goal of testing is not to pass or fail but to identify weaknesses for improvement. It validates technical procedures, confirms team readiness, and measures performance against the RTOs and RPOs established in your Business Impact Analysis.
- Tabletop Exercises: A discussion-based session where the recovery team talks through a simulated disaster scenario, step by step, to identify procedural gaps.
- Full-Scale Failover: A comprehensive test that involves switching over to your secondary recovery site and systems, providing the ultimate validation of your plan's effectiveness.
For example, a financial institution might conduct quarterly tabletop exercises to review its response to a data breach scenario, followed by an annual full-scale failover test to its secondary data center. This layered approach ensures both procedural and technical readiness are maintained.
Key Insight: Treat disaster recovery tests as learning opportunities, not audits. The objective is to find and fix problems in a controlled environment before a real disaster forces your hand.
Actionable Tips for Effective DR Testing:
- Start Small, Scale Up: Begin with tabletop exercises to refine procedures and ensure everyone understands their roles before attempting more complex and resource-intensive full-scale tests.
- Measure Against Objectives: During tests, specifically measure the time it takes to recover systems and validate the amount of data loss. Compare these real-world results directly against your established RTO and RPO targets.
- Create a Remediation Process: Document every issue discovered during a test. Assign ownership and deadlines for each remediation item and track them to completion to ensure continuous improvement.
- Involve Third Parties: If your critical systems rely on external vendors or partners, include them in your testing schedule to validate the entire recovery chain, not just your internal components.
8. Establish Data Retention and Archive Policies
A disaster recovery plan is not just about bringing systems back online; it's about managing data throughout its entire lifecycle. Establishing formal data retention and archive policies is a critical component of any disaster recovery planning checklist. These policies dictate how long specific data types are kept, where they are stored, when they are moved to long-term archives, and how they are securely destroyed.
This process ensures you are not just backing up data, but managing it in a way that balances business needs, storage costs, and legal obligations. Properly defined policies prevent the indefinite accumulation of unnecessary data, which can increase backup windows, recovery times, and potential legal liabilities. It provides a clear framework for what data is essential to recover and what can be legally and safely discarded.
How Policies Support Recovery and Compliance
Data retention policies are driven by a combination of business requirements and external regulations. They create a systematic approach to data management that directly supports disaster recovery by reducing the volume of data that needs to be actively managed and restored.
- Compliance: Many industries have strict rules for data retention. For example, financial services firms must often retain transaction records for seven years to comply with SEC regulations, while healthcare organizations may need to keep patient records for the lifetime of the patient plus a set number of years.
- Cost Optimization: By moving older, infrequently accessed data to lower-cost archival storage (like AWS Glacier or Azure Archive), you can significantly reduce the expense and complexity of your primary backup and recovery systems.
For instance, an e-commerce business can archive order histories older than two years while keeping recent transactional data in a more accessible "hot" storage tier. This tiered approach ensures fast recovery for critical, recent data while maintaining long-term records for compliance at a lower cost.
Key Insight: Data retention isn't just a compliance task; it's a strategic lever for optimizing your disaster recovery process. By reducing data clutter, you shrink recovery times and lower the overall cost of your DR solution.
Actionable Tips for Effective Data Retention Policies:
- Consult Legal Experts: Always involve your legal and compliance teams to ensure your retention schedules meet all relevant industry, national, and international regulations like GDPR or HIPAA.
- Classify Your Data: Categorize data based on its type, sensitivity, and required retention period. This allows you to apply different policies to different datasets, from financial records to marketing analytics.
- Automate Where Possible: Implement automated systems that can enforce retention rules, moving data between storage tiers and flagging it for secure deletion when its lifecycle ends. This reduces manual error and ensures consistent policy application.
- Document and Train: Clearly document all policies and procedures. Ensure that all relevant staff, from IT to legal, understand their roles and responsibilities in managing the data lifecycle.
9. Create a Disaster recovery Budget and Secure Executive Sponsorship
A disaster recovery plan, no matter how well-designed, is purely theoretical without the financial resources and leadership support to implement it. This step in the disaster recovery planning checklist focuses on translating your plan into a formal budget and securing the necessary C-suite sponsorship to bring it to life and sustain it over time.
Securing a budget is more than just asking for money; it involves building a compelling business case that clearly articulates the financial risks of inaction versus the costs of protection. This process transforms disaster recovery from an IT expense into a strategic business investment, ensuring its long-term viability and alignment with organizational goals.
How a Budget Establishes Recovery Realities
A well-defined budget and executive sponsorship provide the practical foundation for every other element of your plan. They determine the tools you can afford, the personnel you can allocate, and the frequency with which you can test your defenses.
- Cost of Inaction: The potential financial loss from downtime, data loss, and reputational damage. This figure is derived directly from your Business Impact Analysis (BIA).
- Cost of Investment: The total cost of implementing the DR plan, including software, hardware, cloud services, personnel, training, and ongoing maintenance.
For example, many large enterprises budget between 2-8% of their total IT spending for business continuity and disaster recovery. Conversely, a startup might leverage a pay-as-you-go cloud DR service to minimize upfront costs while still protecting critical assets, demonstrating to investors and early customers that they have a resilient operational framework.
Key Insight: Executive sponsorship is just as critical as the budget itself. A C-level sponsor (like a CIO or COO) acts as a champion for the DR plan, ensuring it remains a priority, receives adequate funding during annual budget cycles, and has visibility across the entire organization.
Actionable Tips for an Effective Budget and Sponsorship:
- Quantify Downtime Costs: Use data from your BIA to present a clear, quantifiable cost of downtime per hour for critical systems. Frame the DR budget as an insurance policy against this much larger potential loss.
- Present a Phased Approach: If the total cost is high, propose a multi-phase implementation. Start with protecting Tier 1, mission-critical systems first to show immediate value and spread the investment over several quarters.
- Highlight Compliance and Insurance: Frame the budget as a necessity for meeting regulatory requirements (e.g., from the FDIC or OCC for financial institutions) or for satisfying cybersecurity insurance policy mandates.
- Document Everything: Include all potential costs in your proposal: software licensing, cloud consumption fees, specialized staff training, regular testing, and third-party consultant fees. A transparent budget builds trust.
10. Implement Monitoring, Alerting, and Incident Detection Systems
A disaster recovery plan is most effective when activated early. Proactive monitoring and alerting systems act as the digital nervous system for your organization, providing the critical, real-time awareness needed to detect potential disasters before they fully materialize. These automated systems continuously watch your infrastructure, applications, and data for anomalies, triggering immediate alerts when predefined thresholds are breached.
This shift from a reactive to a proactive stance is a cornerstone of a modern disaster recovery planning checklist. Instead of discovering a system failure hours later through user complaints, an automated alert can notify the appropriate team within seconds. This rapid detection drastically shortens the time between an incident's start and the initiation of your recovery protocol, minimizing potential damage and downtime.
How Monitoring Enables Rapid Response
Effective incident detection is about more than just knowing a server is down. It involves establishing a baseline of normal performance and then creating intelligent alerts for deviations from that norm. This allows you to catch subtle issues, like a slow database query or unusual network traffic, that could be precursors to a larger failure.
- Detection: Systems like Datadog, Splunk, or AWS CloudWatch continuously collect metrics and logs from every corner of your IT environment.
- Alerting: When a metric (e.g., CPU usage, backup job failure, replication lag) crosses a critical threshold, an alert is automatically sent via a tool like PagerDuty or Opsgenie.
- Escalation: The alert is routed to the on-call engineer. If there is no response within a set time, it is automatically escalated to the next person or team in the chain, ensuring a swift response.
For example, a monitoring system can detect that a primary database server is no longer responding. It can then automatically trigger an alert to the database team and simultaneously notify the network team, kickstarting the investigation and recovery process in moments.
Key Insight: Monitoring and alerting are not just for preventing disasters; they are essential for validating recovery. After a failover, these systems provide immediate confirmation that the recovery site and its applications are performing as expected.
Actionable Tips for Effective Monitoring:
- Define Smart Thresholds: Set clear, data-driven thresholds for alerts to avoid "alert fatigue" from false positives. A server at 80% CPU usage might be normal, but at 99% for over 10 minutes is a problem.
- Integrate with Incident Management: Connect your alerting tools directly to your incident management system (like ServiceNow or Jira) to automatically create tickets and track resolution progress.
- Monitor the Entire Stack: Ensure you have comprehensive visibility across infrastructure, applications, databases, and network connectivity, including the health of your backup and recovery sites.
- Use Synthetic Monitoring: Proactively test critical user journeys (e.g., logging in, completing a purchase) from different locations to detect issues before your actual users do.
10-Point Disaster Recovery Checklist Comparison
| Activity | Implementation complexity | Resource requirements | Expected outcomes | Ideal use cases | Key advantages |
|---|---|---|---|---|---|
| Conduct a Business Impact Analysis (BIA) | Medium - High - thorough, cross‑departmental work | Stakeholder interviews, financial data, analysts, time | RTO/RPO metrics, prioritized recovery tiers, quantified downtime cost | Initial DR program design, prioritization, compliance | Data-driven priorities, aligns recovery to business needs |
| Establish a Disaster Recovery Team and Define Roles | Medium - organizational design and training | Assigned personnel, training time, coordination tools | Clear chain of command, faster decisions, accountability | Incident coordination, complex organizations, 24/7 ops | Reduces confusion, improves response coordination |
| Create a Backup and Recovery Strategy | Medium - High - technical configuration and policies | Backup software, storage, bandwidth, encryption, staff | Multiple recovery points, faster restorations, lower RPO | Data protection, ransomware defense, regulatory compliance | Protects against data loss, enables quick recovery |
| Document Critical Systems and Dependencies | High - extensive inventorying and mapping | Discovery tools, subject‑matter experts, documentation platform | Accurate dependency maps, recovery sequencing, reduced surprises | Complex IT estates, audit readiness, change management | Enables precise recovery sequencing, reveals single points of failure |
| Identify and Secure Alternate Recovery Sites | High - facilities, contracts, synchronization | Recovery site (hot/warm/cold) or cloud capacity, networking, licenses | Operational continuity, reduced recovery time, geographic diversity | Near‑zero downtime needs, regional risk mitigation | Rapid failover capability, scalable cloud options, geographic resiliency |
| Develop Communication and Notification Procedures | Low - Medium - templates and coordination | Communication platforms, contact lists, PR/legal input | Clear stakeholder updates, controlled messaging, regulatory notices | Customer‑facing incidents, data breaches, regulatory events | Maintains reputation, ensures legal notifications, reduces panic |
| Test and Validate Disaster Recovery Plans | High - exercises, possible production impact | Test environments, staff time, vendor participation, reporting | Validated RTO/RPO, identified gaps, remediation actions | Mature DR programs, pre‑audit, high‑risk systems | Reveals weaknesses, builds confidence, demonstrates compliance |
| Establish Data Retention and Archive Policies | Medium - policy design and tooling | Archive storage, classification tools, legal/compliance support | Compliance with retention laws, cost‑controlled storage, audit trails | Regulated industries, long‑term record keeping, forensic needs | Ensures legal compliance, reduces storage cost, protects privacy |
| Create a Disaster Recovery Budget and Secure Executive Sponsorship | Medium - business case and stakeholder buy‑in | BIA inputs, financial modeling, executive engagement | Approved funding, sustained program support, prioritized spending | Launching or scaling DR programs, long‑term planning | Secures resources, aligns leadership, enables continuity investments |
| Implement Monitoring, Alerting, and Incident Detection Systems | Medium - High - tooling and tuning | Monitoring/alerting tools, operations staff, integrations | Early detection, reduced MTTD, actionable alerts and trends | Proactive incident management, hybrid/cloud environments | Early warning, continuous visibility, faster incident response |
From Checklist to Confidence: Turning Your Plan into Action
Completing a comprehensive disaster recovery planning checklist is a significant achievement, but it marks the beginning of a journey, not the end. The detailed steps we've explored, from conducting a Business Impact Analysis (BIA) to implementing robust monitoring systems, are not one-time tasks. They are the foundational components of a living, breathing strategy that must evolve alongside your organization. The true goal is to transform this document from a static artifact into an active, ingrained part of your operational culture.
This transition from paper to practice is where genuine organizational resilience is forged. A plan that sits on a shelf is merely a theoretical exercise. A plan that is regularly tested, refined, and understood by every member of your disaster recovery team becomes a powerful tool for survival and continuity.
Key Takeaways: From Planning to Proactive Resilience
As you move forward, keep these core principles at the forefront of your strategy. They represent the shift from simply having a disaster recovery plan to building a resilient organization.
-
Resilience is a Cycle, Not a Destination: Your initial plan is a snapshot in time. Technology changes, personnel turns over, and new threats emerge. Embracing a continuous cycle of review, testing, and refinement ensures your plan remains relevant and effective. Treat your disaster recovery plan as an active program, not a passive document.
-
People Power the Plan: A technically perfect plan will fail if the people responsible for executing it are unaware or untrained. The clarity of roles, the effectiveness of your communication strategy, and the quality of your training are just as critical as your backup technology. Empower your team through regular drills and clear documentation.
-
Testing is Non-Negotiable: The only way to know if your disaster recovery plan works is to test it. From tabletop exercises to full-scale simulations, testing uncovers hidden dependencies, process gaps, and flawed assumptions before a real disaster strikes. Each test is an invaluable learning opportunity that strengthens your response capabilities.
Actionable Next Steps to Solidify Your Strategy
With your disaster recovery planning checklist complete, focus on these immediate actions to embed the plan into your organization's DNA and ensure its long-term success.
- Schedule Your First Review: Don't wait. Put the first quarterly or semi-annual review on the calendar now. This sets the precedent that the plan is a dynamic tool requiring regular attention.
- Conduct a Tabletop Exercise: Within the next 90 days, schedule a low-impact tabletop exercise. Gather your DR team and walk through a specific disaster scenario, such as a ransomware attack or a primary data center outage. This is the best way to validate your documented procedures and communication plans in a controlled environment.
- Secure Ongoing Budget and Executive Buy-In: Use the momentum from creating the plan to secure a dedicated, ongoing budget for maintenance, testing, and training. Present the plan to executive leadership not as a cost center, but as a critical investment in business continuity and brand protection.
Ultimately, a well-executed disaster recovery plan is more than just a technical safeguard; it's a competitive advantage. It provides your employees, customers, and partners with the confidence that your organization is stable, reliable, and prepared to weather any storm. By moving beyond the checklist and fostering a culture of preparedness, you ensure that your business is not just built to succeed, but built to last.
Navigating the complexities of modern disaster recovery, especially in cloud-native and hybrid environments, requires specialized expertise. If you're looking to accelerate your journey from planning to proven readiness, Pratt Solutions offers expert consulting and implementation services. We help businesses build robust, automated, and scalable recovery strategies that turn a checklist into true confidence. Visit Pratt Solutions to learn how we can fortify your business against disruption.